zhaohongri’s Curriculum Vitae
Cloud Security Solutions Architect
📧 flashoop@gmail.com | 📱 +60 17 203 2066 / +86 158 1127 0428
📍 Kuala Lumpur, Malaysia | 🎓 B.S. Computer Science | 💼 18 Years Experience
Accomplished Cloud Security Solutions Architect with over 18 years of IT experience and 10+ years specializing in cloud security across AWS, Azure, and GCP platforms. Proven track record managing cloud security products at Alibaba Cloud and Huawei Cloud, with expertise in Anti-DDoS defense, Identity and Access Management (IAM), penetration testing, and regulatory compliance (GDPR, PCI-DSS, R155).
Successfully delivered $25M+ in security solutions revenue for enterprise clients across APAC, Middle East, and LATAM regions, including financial services, Web3, and automotive sectors. Holder of multiple elite certifications including CISSP, CCSP, OSCP, OSEP, GCPN, and AWS certifications.
Cloud Security: AWS Security Specialist | Azure & GCP Security | Anti-DDoS Defense Architecture | IAM Design & Implementation
Cybersecurity: Penetration Testing (OSCP, OSEP, GCPN) | Vulnerability Assessment | Security Architecture | Threat Detection & Response
Compliance & Governance: GDPR | PCI-DSS | R155 | PDPA | SOC 2 | ISO 27001 | CIPP/E Certified
Technical Skills: Cloud Native Security | Network Security | Application Security | DevSecOps | Security Automation
Huawei Cloud Computing Technology Co., Ltd. | December 2016 - Present
Architected and delivered comprehensive cloud security solutions for customers across Asia Pacific, Middle East, Africa, and Latin America, generating over $25M USD in security revenue
Spearheaded security and compliance solutions for Fintech, Web3, and automotive sectors, serving high-profile clients including:
Financial Services: Green Link Bank (Singapore), Asia Pacific Exchange APEX (Singapore)
Cryptocurrency Exchanges: Gate.io (Middle East), BitMar (Middle East)
Enterprise: Astro (Malaysia), Sunway (Malaysia)
Led compliance consulting engagements for GDPR, PDPA, PCI-DSS, and R155 standards
Designed and implemented Internet of Vehicles (IoV) security solutions for Chinese automotive manufacturers expanding globally, including Great Wall Motors, BAIC Foton, and GreatWall Automobile
Developed IoV KPI monitoring solutions and Vehicle Security Operations Center (VSOC) architectures
Anti-DDoS Product Management:
Led the DDoS Defense Design Team for Huawei Cloud Anti-DDoS Service, defining product strategy and technical architecture
Designed public cloud network defense platform solutions and BGP proxy broadcast infrastructure for DDoS mitigation
Architected enhanced DDoS attack detection and defense solutions for Huawei Cloud Internet egress networks
Built Advanced Anti-DDoS solutions for overseas edge security deployments
Identity and Access Management (IAM) Product Management:
Managed IAM service product development, delivering critical features including:
Fine-grained authorization and access control
Global cloud IAM architecture
Enterprise project management capabilities
GDPR compliance features and privacy controls
Cloud Security Product Management Department | February 2013 - December 2016 | Hangzhou, China
Product Manager for Alibaba Cloud’s Advanced Anti-DDoS service, the company’s flagship cloud security offering
Drove product strategy for Advanced Anti-DDoS, which generated over 60% of total cloud security service revenue
Defined product roadmap, feature prioritization, and go-to-market strategies for enterprise DDoS protection
Collaborated with engineering teams to deliver industry-leading DDoS mitigation capabilities
Conducted competitive analysis and positioned Alibaba Cloud as a leader in cloud security market
Enterprise Security Product Division | September 2006 - December 2013 | Beijing, China
Product Manager at China’s largest security company, responsible for enterprise security product portfolio
Founded and led 360 Website Guard, one of China’s pioneering cloud security protection services competing with CloudFlare
Managed cross-functional team of 10+ members, delivering security services to 100,000+ customers
Drove product innovation in web application firewall (WAF) and DDoS protection technologies
Established early-stage cloud security product-market fit in the Chinese enterprise market
Gaming Sector Specialist:
Lead security architect for top-tier gaming clients including Tencent Games (LATAM), Lilith Games, and 37 Interactive Entertainment (三七互娱).
Designed robust architectures to defend against Tbps-level DDoS attacks while maintaining ultra-low latency (<50ms) for global players.
Financial Services & Web3 Security
Architected cloud security infrastructure for Singapore’s Green Link Bank and APEX Exchange
Designed high-availability, DDoS-resistant architectures for cryptocurrency exchanges serving Middle East markets
Implemented PCI-DSS compliant cloud environments for payment processing systems
Automotive IoV Compliance Solutions
Delivered R155 compliance architecture for multiple Chinese automotive manufacturers expanding to international markets
Designed Vehicle Security Operations Center (VSOC) for real-time threat monitoring and incident response
Implemented security KPI frameworks aligned with automotive cybersecurity regulations
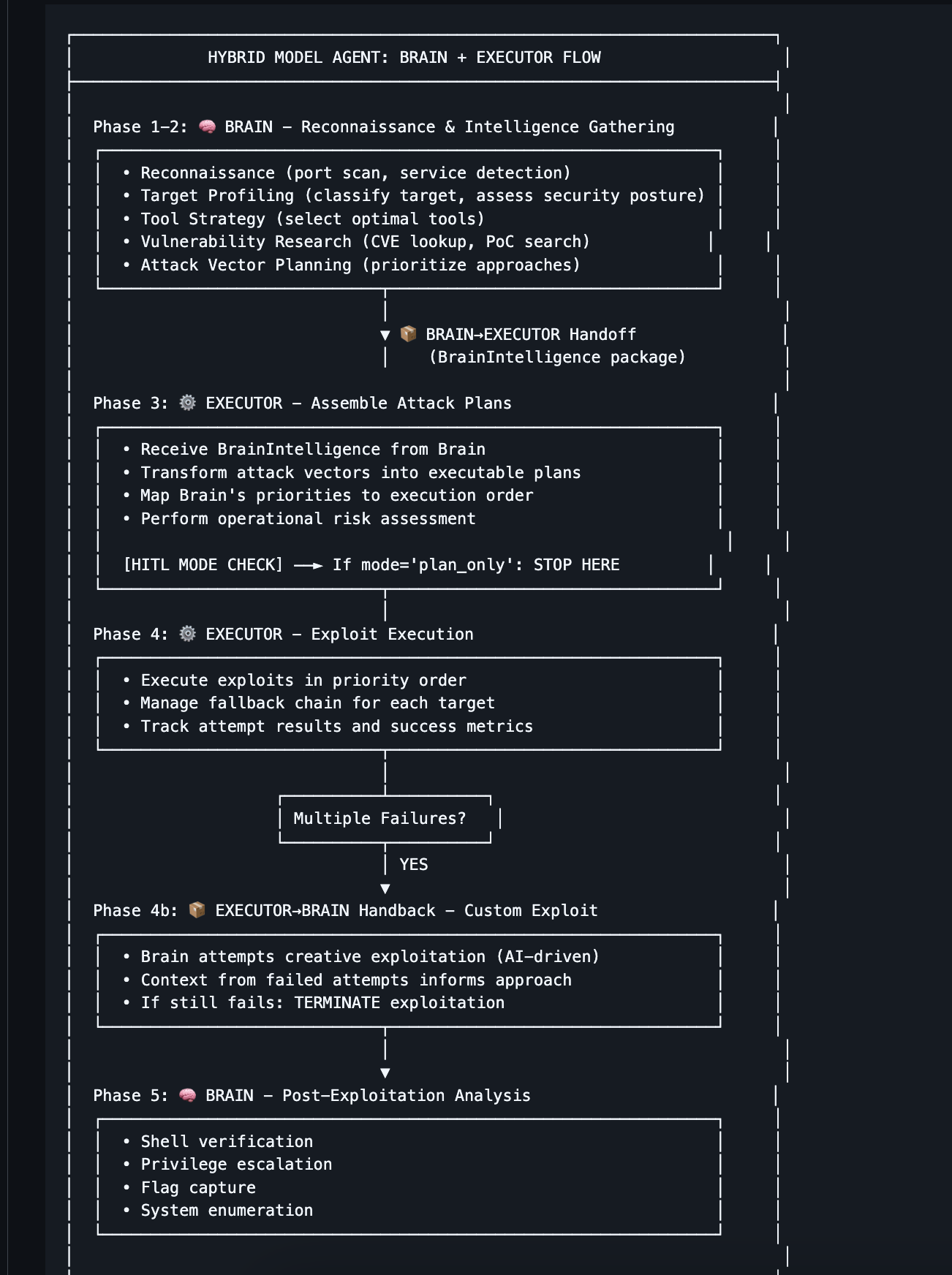
CyberDiagram - Security Audit Specialist Agent
AI-driven automated security audit platform integrating professional penetration testing tools with intelligent decision-making capabilities using Claude AI and Model Context Protocol (MCP).
Key Features:
Automated Reconnaissance: Network scanning, port discovery, service enumeration via Nmap integration
Vulnerability Research: Exploit-DB and Metasploit framework integration
AI-Driven Analysis: Intelligent workflow orchestration and vulnerability prioritization
Compliance Logging: SOC 2 and ISO 27001 compliant audit trails
Professional Reporting: Automated Markdown-based security assessment reports
Security Controls: Authorization validation, rate limiting, comprehensive audit logging
Architecture: Hybrid Brain + Executor model separating cognitive planning from operational execution
Technology Stack: Claude AI, Model Context Protocol, Nmap, Metasploit, Exploit-DB


Snapano - Network Asset Visualization Platform
Data visualization platform for simplified asset management and compliance reporting. Enables online management of network assets through interactive topology visualization.
Technology Stack: React, Three.js, WebGL
GitHub Repositories:
Demo: YouTube Video
CISSP - Certified Information Systems Security Professional

CCSP - Certified Cloud Security Professional

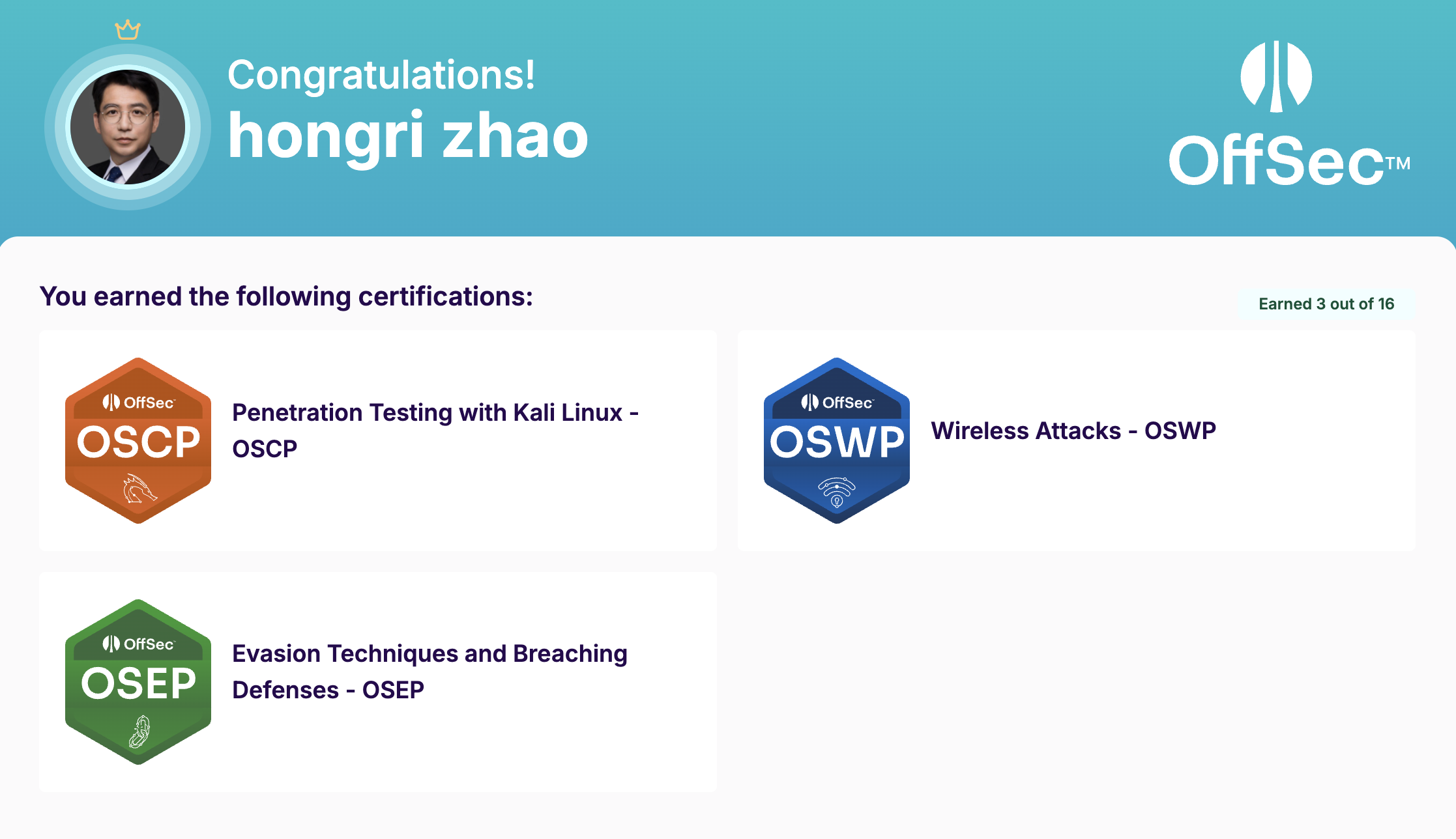
OSCP - OffSec Certified Professional (Penetration Testing)
OSEP - OffSec Experienced Penetration Tester (Advanced Exploitation)
GCPN - GIAC Cloud Penetration Tester

AWS Certified Solutions Architect - Professional
AWS Certified Security - Specialty
AWS Certified Advanced Networking - Specialty
CIPP/E - Certified Information Privacy Professional/Europe (GDPR)

Bachelor of Science in Computer Science
University Name | Graduation Year
English: Upper Intermediate (B2) - Professional Working Proficiency
TOEIC Listening & Reading: 780
TOEIC Speaking: 130
Proficient in technical documentation and business communication
Mandarin Chinese: Native Proficiency
Target Positions:
Cloud Security Solutions Architect
Cloud Infrastructure Security Engineer
Cloud Penetration Tester
Security Architecture Lead
Preferred Locations:
Asia Pacific Region
Other International Markets
Cloud Platforms: AWS, Azure, Google Cloud Platform (GCP), Huawei Cloud, Alibaba Cloud
Security Tools: Metasploit, Nmap, Burp Suite, Wireshark, Exploit-DB, DirBuster
Programming/Scripting: Python, JavaScript/TypeScript, React, Node.js, Shell Scripting
Security Frameworks: NIST, ISO 27001, SOC 2, CIS Controls, OWASP Top 10
Networking: BGP, TCP/IP, DNS, Load Balancing, CDN, DDoS Mitigation
DevSecOps: CI/CD Security, Container Security, Infrastructure as Code (IaC)
References available upon request